Search results for: Cover Text
712 Labeling Method in Steganography
Authors: H. Motameni, M. Norouzi, M. Jahandar, A. Hatami
Abstract:
In this paper a way of hiding text message (Steganography) in the gray image has been presented. In this method tried to find binary value of each character of text message and then in the next stage, tried to find dark places of gray image (black) by converting the original image to binary image for labeling each object of image by considering on 8 connectivity. Then these images have been converted to RGB image in order to find dark places. Because in this way each sequence of gray color turns into RGB color and dark level of grey image is found by this way if the Gary image is very light the histogram must be changed manually to find just dark places. In the final stage each 8 pixels of dark places has been considered as a byte and binary value of each character has been put in low bit of each byte that was created manually by dark places pixels for increasing security of the main way of steganography (LSB).
Keywords: Binary image, labeling, low bit, neighborhood, RGB image, steganography, threshold.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 2137711 Data Hiding in Images in Discrete Wavelet Domain Using PMM
Authors: Souvik Bhattacharyya, Gautam Sanyal
Abstract:
Over last two decades, due to hostilities of environment over the internet the concerns about confidentiality of information have increased at phenomenal rate. Therefore to safeguard the information from attacks, number of data/information hiding methods have evolved mostly in spatial and transformation domain.In spatial domain data hiding techniques,the information is embedded directly on the image plane itself. In transform domain data hiding techniques the image is first changed from spatial domain to some other domain and then the secret information is embedded so that the secret information remains more secure from any attack. Information hiding algorithms in time domain or spatial domain have high capacity and relatively lower robustness. In contrast, the algorithms in transform domain, such as DCT, DWT have certain robustness against some multimedia processing.In this work the authors propose a novel steganographic method for hiding information in the transform domain of the gray scale image.The proposed approach works by converting the gray level image in transform domain using discrete integer wavelet technique through lifting scheme.This approach performs a 2-D lifting wavelet decomposition through Haar lifted wavelet of the cover image and computes the approximation coefficients matrix CA and detail coefficients matrices CH, CV, and CD.Next step is to apply the PMM technique in those coefficients to form the stego image. The aim of this paper is to propose a high-capacity image steganography technique that uses pixel mapping method in integer wavelet domain with acceptable levels of imperceptibility and distortion in the cover image and high level of overall security. This solution is independent of the nature of the data to be hidden and produces a stego image with minimum degradation.Keywords: Cover Image, Pixel Mapping Method (PMM), StegoImage, Integer Wavelet Tranform.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 2852710 MHD Stagnation Point Flow towards a Shrinking Sheet with Suction in an Upper-Convected Maxwell (UCM) Fluid
Authors: K. Jafar, R. Nazar, A. Ishak, I. Pop
Abstract:
The present analysis considers the steady stagnation point flow and heat transfer towards a permeable shrinking sheet in an upper-convected Maxwell (UCM) electrically conducting fluid, with a constant magnetic field applied in the transverse direction to flow and a local heat generation within the boundary layer, with a heat generation rate proportional to (T-T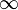 )p Using a similarity transformation, the governing system of partial differential equations is first transformed into a system of ordinary differential equations, which is then solved numerically using a finite-difference scheme known as the Keller-box method. Numerical results are obtained for the flow and thermal fields for various values of the stretching/shrinking parameter λ, the magnetic parameter M, the elastic parameter K, the Prandtl number Pr, the suction parameter s, the heat generation parameter Q, and the exponent p. The results indicate the existence of dual solutions for the shrinking sheet up to a critical value λc whose value depends on the value of M, K, and s. In the presence of internal heat absorption (Q<0) the surface heat transfer rate decreases with increasing p but increases with parameters Q and s when the sheet is either stretched or shrunk.
)p Using a similarity transformation, the governing system of partial differential equations is first transformed into a system of ordinary differential equations, which is then solved numerically using a finite-difference scheme known as the Keller-box method. Numerical results are obtained for the flow and thermal fields for various values of the stretching/shrinking parameter λ, the magnetic parameter M, the elastic parameter K, the Prandtl number Pr, the suction parameter s, the heat generation parameter Q, and the exponent p. The results indicate the existence of dual solutions for the shrinking sheet up to a critical value λc whose value depends on the value of M, K, and s. In the presence of internal heat absorption (Q<0) the surface heat transfer rate decreases with increasing p but increases with parameters Q and s when the sheet is either stretched or shrunk.
Keywords: Magnetohydrodynamic (MHD), boundary layer flow, UCM fluid, stagnation point, shrinking sheet.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 2068709 A Relationship Extraction Method from Literary Fiction Considering Korean Linguistic Features
Authors: Hee-Jeong Ahn, Kee-Won Kim, Seung-Hoon Kim
Abstract:
The knowledge of the relationship between characters can help readers to understand the overall story or plot of the literary fiction. In this paper, we present a method for extracting the specific relationship between characters from a Korean literary fiction. Generally, methods for extracting relationships between characters in text are statistical or computational methods based on the sentence distance between characters without considering Korean linguistic features. Furthermore, it is difficult to extract the relationship with direction from text, such as one-sided love, because they consider only the weight of relationship, without considering the direction of the relationship. Therefore, in order to identify specific relationships between characters, we propose a statistical method considering linguistic features, such as syntactic patterns and speech verbs in Korean. The result of our method is represented by a weighted directed graph of the relationship between the characters. Furthermore, we expect that proposed method could be applied to the relationship analysis between characters of other content like movie or TV drama.
Keywords: Data mining, Korean linguistic feature, literary fiction, relationship extraction.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 1795708 Examining the Dubbing Strategies Used in the Egyptian Dubbed Version of Mulan (1998)
Authors: Shaza Melies, Saadeya Salem, Seham Kareh
Abstract:
Cartoon films are multisemiotic as various modes integrate in the production of meaning. This study aims to examine the cultural and linguistic specific references in the Egyptian dubbed cartoon film Mulan. The study examines the translation strategies implemented in the Egyptian dubbed version of Mulan to meet the cultural preferences of the audience. The study reached the following findings: Using the traditional translation strategies does not deliver the intended meaning of the source text and causes loss in the intended humor. As a result, the findings showed that in the dubbed version, translators tend to omit, change, or add information to the target text to be accepted by the audience. The contrastive analysis of the Mulan (English and dubbed versions) proves the connotations that the dubbing has taken to be accepted by the target audience. Cartoon films are multisemiotic as various modes integrate in the production of meaning. This study aims to examine the cultural and linguistic specific references in the Egyptian dubbed cartoon film Mulan. The study examines the translation strategies implemented in the Egyptian dubbed version of Mulan to meet the cultural preferences of the audience. The study reached the following findings: Using the traditional translation strategies does not deliver the intended meaning of the source text and causes loss in the intended humor. As a result, the findings showed that in the dubbed version, translators tend to omit, change, or add information to the target text to be accepted by the audience. The contrastive analysis of the Mulan (English and dubbed versions) proves the connotations that the dubbing has taken to be accepted by the target audience.Keywords: Domestication, dubbing, Mulan, translation theories.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 733707 Concepts Extraction from Discharge Notes using Association Rule Mining
Authors: Basak Oguz Yolcular
Abstract:
A large amount of valuable information is available in plain text clinical reports. New techniques and technologies are applied to extract information from these reports. In this study, we developed a domain based software system to transform 600 Otorhinolaryngology discharge notes to a structured form for extracting clinical data from the discharge notes. In order to decrease the system process time discharge notes were transformed into a data table after preprocessing. Several word lists were constituted to identify common section in the discharge notes, including patient history, age, problems, and diagnosis etc. N-gram method was used for discovering terms co-Occurrences within each section. Using this method a dataset of concept candidates has been generated for the validation step, and then Predictive Apriori algorithm for Association Rule Mining (ARM) was applied to validate candidate concepts.Keywords: association rule mining, otorhinolaryngology, predictive apriori, text mining
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 1614706 A Multiple Beam LTE Base Station Antenna with Simultaneous Vertical and Horizontal Sectorization
Authors: Mohamed Sanad, Noha Hassan
Abstract:
A low wind-load light-weight broad-band multi-beam base station antenna has been developed. It can generate any required number of beams with the required beamwidths. It can have horizontal and vertical sectorization at the same time. Vertical sectorization doubles the overall number of beams. It will be very valuable in LTE-A and 5G. It can be used to serve vertically split inner and outer cells, which improves system performance. The intersection between the beams of the proposed multi-beam antenna can be controlled by optimizing the design parameters of the antenna. The gain at the points of intersection between the beams, the null filling and the overlap between the beams can all be modified. The proposed multi-beam base station antenna can cover an unlimited number of wireless applications, regardless of their frequency bands. It can simultaneously cover all, current and future, wireless technology generations such as 2G, 3G, 4G (LTE), --- etc. For example, in LTE, it covers the bands 450-470 MHz, 690-960 MHz, 1.4-2.7 GHz and 3.3-3.8 GHz. It has at least 2 ports for each band in each beam for ±45° polarizations. It can include up to 72 ports or even more, which could facilitate any further needed capacity expansions.
Keywords: Base station antenna, multi-beam antenna, smart antenna, vertical sectorization.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 2026705 Graphical Password Security Evaluation by Fuzzy AHP
Authors: Arash Habibi Lashkari, Azizah Abdul Manaf, Maslin Masrom
Abstract:
In today's day and age, one of the important topics in information security is authentication. There are several alternatives to text-based authentication of which includes Graphical Password (GP) or Graphical User Authentication (GUA). These methods stems from the fact that humans recognized and remembers images better than alphanumerical text characters. This paper will focus on the security aspect of GP algorithms and what most researchers have been working on trying to define these security features and attributes. The goal of this study is to develop a fuzzy decision model that allows automatic selection of available GP algorithms by taking into considerations the subjective judgments of the decision makers who are more than 50 postgraduate students of computer science. The approach that is being proposed is based on the Fuzzy Analytic Hierarchy Process (FAHP) which determines the criteria weight as a linear formula.Keywords: Graphical Password, Authentication Security, Attack Patterns, Brute force attack, Dictionary attack, Guessing Attack, Spyware attack, Shoulder surfing attack, Social engineering Attack, Password Entropy, Password Space.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 1936704 Evaluating some Feature Selection Methods for an Improved SVM Classifier
Authors: Daniel Morariu, Lucian N. Vintan, Volker Tresp
Abstract:
Text categorization is the problem of classifying text documents into a set of predefined classes. After a preprocessing step the documents are typically represented as large sparse vectors. When training classifiers on large collections of documents, both the time and memory restrictions can be quite prohibitive. This justifies the application of features selection methods to reduce the dimensionality of the document-representation vector. Four feature selection methods are evaluated: Random Selection, Information Gain (IG), Support Vector Machine (called SVM_FS) and Genetic Algorithm with SVM (GA_FS). We showed that the best results were obtained with SVM_FS and GA_FS methods for a relatively small dimension of the features vector comparative with the IG method that involves longer vectors, for quite similar classification accuracies. Also we present a novel method to better correlate SVM kernel-s parameters (Polynomial or Gaussian kernel).
Keywords: Features selection, learning with kernels, support vector machine, genetic algorithms and classification.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 1538703 Image Adaptive Watermarking with Visual Model in Orthogonal Polynomials based Transformation Domain
Authors: Krishnamoorthi R., Sheba Kezia Malarchelvi P. D.
Abstract:
In this paper, an image adaptive, invisible digital watermarking algorithm with Orthogonal Polynomials based Transformation (OPT) is proposed, for copyright protection of digital images. The proposed algorithm utilizes a visual model to determine the watermarking strength necessary to invisibly embed the watermark in the mid frequency AC coefficients of the cover image, chosen with a secret key. The visual model is designed to generate a Just Noticeable Distortion mask (JND) by analyzing the low level image characteristics such as textures, edges and luminance of the cover image in the orthogonal polynomials based transformation domain. Since the secret key is required for both embedding and extraction of watermark, it is not possible for an unauthorized user to extract the embedded watermark. The proposed scheme is robust to common image processing distortions like filtering, JPEG compression and additive noise. Experimental results show that the quality of OPT domain watermarked images is better than its DCT counterpart.Keywords: Orthogonal Polynomials based Transformation, Digital Watermarking, Copyright Protection, Visual model.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 1696702 Skin Effect: A Natural Phenomenon for Minimization of Ground Bounce in VLSI RC Interconnect
Authors: Shilpi Lavania
Abstract:
As the frequency of operation has attained a range of GHz and signal rise time continues to increase interconnect technology is suffering due to various high frequency effects as well as ground bounce problem. In some recent studies a high frequency effect i.e. skin effect has been modeled and its drawbacks have been discussed. This paper strives to make an impression on the advantage side of modeling skin effect for interconnect line. The proposed method has considered a CMOS with RC interconnect. Delay and noise considering ground bounce problem and with skin effect are discussed. The simulation results reveal an advantage of considering skin effect for minimization of ground bounce problem during the working of the model. Noise and delay variations with temperature are also presented.
Keywords: Interconnect, Skin effect, Ground Bounce, Delay, Noise.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 3138701 Future Logistics - Challenges, Requirements and Solutions for Logistics Networks
Authors: Martin Roth, Axel Klarmann, Bogdan Franczyk
Abstract:
The importance of logistics has changed enormously in the last few decades. While logistics was formerly one of the core functions of most companies, logistics or at least parts of their functions are nowadays outsourced to external logistic service providers in terms of contracts. As a result of this shift new business models like the fourth party logistics provider emerged, which designs, plans and monitors the resulting logistics networks. This new business model and topics such as Synchromodality or Big Data impose new requirements on the underlying IT, which cannot be met with conventional concepts and approaches. In this paper, the challenges of logistics network monitoring are outlined by using a scenario. The most common layers in a logical multilayered architecture for an information system are used to point out the arising challenges for IT. In addition, first appropriate solution approaches are introduced.
Keywords: Complex Event Processing, Fourth Party Logistics Service Provider, Logistics monitoring, Synchromodality.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 3376700 Composite Kernels for Public Emotion Recognition from Twitter
Authors: Chien-Hung Chen, Yan-Chun Hsing, Yung-Chun Chang
Abstract:
The Internet has grown into a powerful medium for information dispersion and social interaction that leads to a rapid growth of social media which allows users to easily post their emotions and perspectives regarding certain topics online. Our research aims at using natural language processing and text mining techniques to explore the public emotions expressed on Twitter by analyzing the sentiment behind tweets. In this paper, we propose a composite kernel method that integrates tree kernel with the linear kernel to simultaneously exploit both the tree representation and the distributed emotion keyword representation to analyze the syntactic and content information in tweets. The experiment results demonstrate that our method can effectively detect public emotion of tweets while outperforming the other compared methods.
Keywords: Public emotion recognition, natural language processing, composite kernel, sentiment analysis, text mining.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 773699 Text Mining Analysis of the Reconstruction Plans after the Great East Japan Earthquake
Authors: Minami Ito, Akihiro Iijima
Abstract:
On March 11, 2011, the Great East Japan Earthquake occurred off the coast of Sanriku, Japan. It is important to build a sustainable society through the reconstruction process rather than simply restoring the infrastructure. To compare the goals of reconstruction plans of quake-stricken municipalities, Japanese language morphological analysis was performed by using text mining techniques. Frequently-used nouns were sorted into four main categories of “life”, “disaster prevention”, “economy”, and “harmony with environment”. Because Soma City is affected by nuclear accident, sentences tagged to “harmony with environment” tended to be frequent compared to the other municipalities. Results from cluster analysis and principle component analysis clearly indicated that the local government reinforces the efforts to reduce risks from radiation exposure as a top priority.
Keywords: Eco-friendly reconstruction, harmony with environment, decontamination, nuclear disaster.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 1966698 Features of Soil Formation in the North of Western Siberia in Cryogenic Conditions
Authors: Tatiana V. Raudina, Sergey P. Kulizhskiy
Abstract:
A large part of Russia is located in permafrost areas. These areas are widely used because there are concentrated valuable natural resources. Therefore to explore of cryosols it is important due to the significant increase of anthropogenic stress as well as the problem of global climate change. In the north of Western Siberia permafrost phenomena is widespread. Permafrost as a factor of soil formation and cryogenesis as a process have a great impact on the soil formation of these areas. Based on the research results of permafrost-affected soils tundra landscapes formed in the central part of the Tazovskiy Peninsula in cryogenic conditions, data were obtained which characterize the morphological features of soils. The specificity of soil cover distribution and manifestation of soil-forming processes within the study area are noted. Permafrost features such as frost cracking, cryoturbation, thixotropy, movement of humus are formed. The formation of these features is increased with the development of the territory. As a consequence, there is a change in the components of the environment and the destruction of the soil cover.
Keywords: Gleyed and nongleyed soils, permafrost, soil cryogenesis (pedocryogenesis), soil-forming macroprocesses.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 2062697 Use and Relationship of Shell Nouns as Cohesive Devices in the Quality of Second Language Writing
Authors: Kristine D. de Leon, Junifer A. Abatayo, Jose Cristina M. Pariña
Abstract:
The current study is a comparative analysis of the use of shell nouns as a cohesive device (CD) in an English for Second Language (ESL) setting in order to identify their use and relationship in the quality of second language (L2) writing. As these nouns were established to anticipate the meaning within, across or outside the text, their use has fascinated writing researchers. The corpus of the study included published articles from reputable journals and graduate students’ papers in order to analyze the frequency of shell nouns using “highly prevalent” nouns in the academic community, to identify the different lexicogrammatical patterns where these nouns occur and to the functions connected with these patterns. The result of the study implies that published authors used more shell nouns in their paper than graduate students. However, the functions of the different lexicogrammatical patterns for the frequently occurring shell nouns are somewhat similar. These results could help students in enhancing the cohesion of their text and in comprehending it.
Keywords: Anaphoric-cataphoric, cohesive device, lexicogrammatical, shell nouns.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 652696 Multi Language Text Editor for Burushaski and Urdu through Unicode
Authors: Irfan Qadir Baig, Muhammad Sharif, Aman Ullah Khan
Abstract:
This paper introduces an isolated and unique ancient language Burushaski, spoken in Hunza, Nagar, Yasin and parts of Gilgit in the Northern Areas of Pakistan. It explains the working mechanism of Multi Language Text Editor for Urdu and Burushaski. It is developed under the use of ISO/IEC 10646 Unicode standards for Urdu and Burushaski open-type fonts. It gives an ample opportunity to this regional ancient language to have a modern Information technology for its promotion and preservation. The main objective of this research paper is to help preserve the heritage of such rare languages and give smart way of automation. It also facilitates to those who are interested in undertaking research on Burushaski or keen to trace fonatic relationship between the national Urdu language and Burushaski. Since this editor covers both Burushaski and Urdu so it can play an important role to introduce Burusho linguistic culture to the world at large. Precisely, as a result of this research paper, Burushaski publication through IT means would be possible.Keywords: Burushaski, Bri Naqsh, Unicode, Burusho, Hunza, Meshaski.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 2107695 Glass Bottle Inspector Based on Machine Vision
Authors: Huanjun Liu, Yaonan Wang, Feng Duan
Abstract:
This text studies glass bottle intelligent inspector based machine vision instead of manual inspection. The system structure is illustrated in detail in this paper. The text presents the method based on watershed transform methods to segment the possible defective regions and extract features of bottle wall by rules. Then wavelet transform are used to exact features of bottle finish from images. After extracting features, the fuzzy support vector machine ensemble is putted forward as classifier. For ensuring that the fuzzy support vector machines have good classification ability, the GA based ensemble method is used to combining the several fuzzy support vector machines. The experiments demonstrate that using this inspector to inspect glass bottles, the accuracy rate may reach above 97.5%.Keywords: Intelligent Inspection, Support Vector Machines, Ensemble Methods, watershed transform, Wavelet Transform
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 3895694 Evaluation of Energy and Environmental Aspects of Reduced Tillage Systems Applied in Maize Cultivation
Authors: E. Sarauskis, L. Masilionyte, Z. Kriauciuniene, K. Romaneckas, S. Buragiene
Abstract:
In maize growing technologies, tillage technological operations are the most time-consuming and require the greatest fuel input. Substitution of conventional tillage, involving deep ploughing, by other reduced tillage methods can reduce technological production costs, diminish soil degradation and environmental pollution from greenhouse gas emissions, as well as improve economic competitiveness of agricultural produce.
Experiments designed to assess energy and environmental aspects associated with different reduced tillage systems, applied in maize cultivation were conducted at Aleksandras Stulginskis University taking into account Lithuania’s economic and climate conditions. The study involved 5 tillage treatments: deep ploughing (DP, control), shallow ploughing (SP), deep cultivation (DC), shallow cultivation (SC) and no-tillage (NT).
Our experimental evidence suggests that with the application of reduced tillage systems it is feasible to reduce fuel consumption by 13-58% and working time input by 8.4% to nearly 3-fold, to reduce the cost price of maize cultivation technological operations, decrease environmental pollution with CO2 gas by 30 to 146 kg ha-1, compared with the deep ploughing.
Keywords: Reduced tillage, energy and environmental assessment, fuel consumption, CO2 emission, maize.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 2094693 Improved Safety Science: Utilizing a Design Hierarchy
Authors: Ulrica Pettersson
Abstract:
Collection of information on incidents is regularly done through pre-printed incident report forms. These tend to be incomplete and frequently lack essential information. ne consequence is that reports with inadequate information, that do not fulfil analysts’ requirements, are transferred into the analysis process. To improve an incident reporting form, theory in design science, witness psychology and interview and questionnaire research has been used. Previously three experiments have been conducted to evaluate the form and shown significant improved results. The form has proved to capture knowledge, regardless of the incidents’ character or context. The aim in this paper is to describe how design science, in more detail a design hierarchy can be used to construct a collection form for improvements in safety science.
Keywords: Design science, data collection, form, incident report, safety science.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 834692 Non-Homogeneous Layered Fiber Reinforced Concrete
Authors: Vitalijs Lusis, Andrejs Krasnikovs
Abstract:
Fiber reinforced concrete is important material for load bearing structural elements. Usually fibers are homogeneously distributed in a concrete body having arbitrary spatial orientations. At the same time, in many situations, fiber concrete with oriented fibers is more optimal. Is obvious, that is possible to create constructions with oriented short fibers in them, in different ways. Present research is devoted to one of such approaches- fiber reinforced concrete prisms having dimensions 100mm ×100mm ×400mmwith layers of non-homogeneously distributed fibers inside them were fabricated.
Simultaneously prisms with homogeneously dispersed fibers were produced for reference as well. Prisms were tested under four point bending conditions. During the tests vertical deflection at the center of every prism and crack opening were measured (using linear displacements transducers in real timescale). Prediction results were discussed.
Keywords: Fiber reinforced concrete, 4-point bending, steel fiber.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 3009691 An Improved Method to Watermark Images Sensitive to Blocking Artifacts
Authors: Afzel Noore
Abstract:
A new digital watermarking technique for images that are sensitive to blocking artifacts is presented. Experimental results show that the proposed MDCT based approach produces highly imperceptible watermarked images and is robust to attacks such as compression, noise, filtering and geometric transformations. The proposed MDCT watermarking technique is applied to fingerprints for ensuring security. The face image and demographic text data of an individual are used as multiple watermarks. An AFIS system was used to quantitatively evaluate the matching performance of the MDCT-based watermarked fingerprint. The high fingerprint matching scores show that the MDCT approach is resilient to blocking artifacts. The quality of the extracted face and extracted text images was computed using two human visual system metrics and the results show that the image quality was high.Keywords: Digital watermarking, data hiding, modified discretecosine transformation (MDCT).
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 1605690 Measuring Text-Based Semantics Relatedness Using WordNet
Authors: Madiha Khan, Sidrah Ramzan, Seemab Khan, Shahzad Hassan, Kamran Saeed
Abstract:
Measuring semantic similarity between texts is calculating semantic relatedness between texts using various techniques. Our web application (Measuring Relatedness of Concepts-MRC) allows user to input two text corpuses and get semantic similarity percentage between both using WordNet. Our application goes through five stages for the computation of semantic relatedness. Those stages are: Preprocessing (extracts keywords from content), Feature Extraction (classification of words into Parts-of-Speech), Synonyms Extraction (retrieves synonyms against each keyword), Measuring Similarity (using keywords and synonyms, similarity is measured) and Visualization (graphical representation of similarity measure). Hence the user can measure similarity on basis of features as well. The end result is a percentage score and the word(s) which form the basis of similarity between both texts with use of different tools on same platform. In future work we look forward for a Web as a live corpus application that provides a simpler and user friendly tool to compare documents and extract useful information.
Keywords: GraphViz representation, semantic relatedness, similarity measurement, WordNet similarity.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 836689 Evaluation of Energy Upgrade Measures and Connection of Renewable Energy Sources Using Software Tools: Case Study of an Academic Library Building in Larissa, Greece
Authors: Giwrgos S. Gkarmpounis, Aikaterini G. Rokkou, Marios N. Moschakis
Abstract:
Increased energy consumption in the academic buildings, creates the need to implement energy saving measures and to take advantage of the renewable energy sources to cover the electrical needs of those buildings. An Academic Library will be used as a case study. With the aid of RETScreen software that takes into account the energy consumptions and characteristics of the Library Building, it is proved that measures such as the replacement of fluorescent lights with led lights, the installation of outdoor shading, the replacement of the openings and Building Management System installation, provide a high level of energy savings. Moreover, given the available space of the building and the climatic data, the installation of a photovoltaic system of 100 kW can also cover a serious amount of the building energy consumption, unlike a wind system that seems uncompromising. Lastly, HOMER software is used to compare the use of a photovoltaic system against a wind system in order to verify the results that came up from the RETScreen software concerning the renewable energy sources.
Keywords: Energy saving measures, homer software, renewable energy sources, RETScreen software, energy efficiency and quality.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 992688 Investigation of Constant Transconductance Circuit for Low Power Low-Noise Amplifier
Authors: Wei Yi Lim, M. Annamalai Arasu, M. Kumarasamy Raja, Minkyu Je
Abstract:
In this paper, the design of wide-swing constant transconductance (gm) bias circuit that generates bias voltage for low-noise amplifier (LNA) circuit design by using an off-chip resistor is demonstrated. The overall transconductance (Gm) generated by the constant gm bias circuit is important to maintain the overall gain and noise figure of the LNA circuit. Therefore, investigation is performed to study the variation in Gm with process, temperature and supply voltage (PVT). Temperature and supply voltage are swept from -10 °C to 85 °C and 1.425 V to 1.575 V respectively, while the process conditions are also varied to the extreme and the gm variation is eventually concluded at between -3 % to 7 %. With the slight variation in the gm value, through simulation, at worst condition of state SS, we are able to attain a conversion gain (S21) variation of -3.10 % and a noise figure (NF) variation of 18.71 %. The whole constant gm circuit draws approximately 100 µA from a 1.5V supply and is designed based on 0.13 µm CMOS process.
Keywords: Transconductance, LNA, temperature, process.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 4130687 AI Tutor: A Computer Science Domain Knowledge Graph-Based QA System on JADE platform
Authors: Yingqi Cui, Changran Huang, Raymond Lee
Abstract:
In this paper, we proposed an AI Tutor using ontology and natural language process techniques to generate a computer science domain knowledge graph and answer users’ questions based on the knowledge graph. We define eight types of relation to extract relationships between entities according to the computer science domain text. The AI tutor is separated into two agents: learning agent and Question-Answer (QA) agent and developed on JADE (a multi-agent system) platform. The learning agent is responsible for reading text to extract information and generate a corresponding knowledge graph by defined patterns. The QA agent can understand the users’ questions and answer humans’ questions based on the knowledge graph generated by the learning agent.
Keywords: Artificial intelligence, natural language process, knowledge graph, agent, QA system.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 894686 Profile Analysis and Experiences on the Tourism of Jalapão State Park, Tocantins, Brazil
Authors: Veruska C. Dutra, Mary L. G. S. Senna, Felipe S. Spindler
Abstract:
The State Park Jalapão - PEJ proved to be one of the protected areas that has attracted tourists from all over the world with its unique scenic landscapes. Although the region already has a considerable tourist flow, to our knowledge there is a lack of continuity of studies in the region capable of drawing a plan of activities, such as the profile of the tourist and analysis of their experiences in the region, carried out from 2006-2007. Therefore, this study was proposed to know the profile and experiences of tourists visiting the park today, making a connection with the earlier study, in order to generate subsidies to trace improvement actions. We conducted interviews with tourists in the main tourism season 2015. The results show that after eight years of carrying out the first study, there were no changes, highlighting the lack of a tourism plan for the park.
Keywords: Jalapão, profile tourist, level of satisfaction.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 1045685 Degraded Document Analysis and Extraction of Original Text Document: An Approach without Optical Character Recognition
Authors: L. Hamsaveni, Navya Prakash, Suresha
Abstract:
Document Image Analysis recognizes text and graphics in documents acquired as images. An approach without Optical Character Recognition (OCR) for degraded document image analysis has been adopted in this paper. The technique involves document imaging methods such as Image Fusing and Speeded Up Robust Features (SURF) Detection to identify and extract the degraded regions from a set of document images to obtain an original document with complete information. In case, degraded document image captured is skewed, it has to be straightened (deskew) to perform further process. A special format of image storing known as YCbCr is used as a tool to convert the Grayscale image to RGB image format. The presented algorithm is tested on various types of degraded documents such as printed documents, handwritten documents, old script documents and handwritten image sketches in documents. The purpose of this research is to obtain an original document for a given set of degraded documents of the same source.Keywords: Grayscale image format, image fusing, SURF detection, YCbCr image format.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 1155684 Ecosystem Post-Wildfire Effects of Thasos Island
Authors: George D. Ranis, Valasia Iakovoglou, George N. Zaimes
Abstract:
Fires is one of the main types of disturbances that shape ecosystems in the Mediterranean region. However nowadays, climate alterations towards higher temperatures result on increased levels of fire intensity, frequency and spread as well as difficulties for natural regeneration to occur. Thasos Island is one of the Greek islands that has experienced those problems. Since 1984, a series of wildfires led to the reduction of forest cover from 61.6% to almost 20%. The negative impacts were devastating in many different aspects for the island. The absence of plant cover, post-wildfire precipitation and steep slopes were the major factors that induced severe soil erosion and intense floods. That also resulted to serious economic problems to the local communities and the inability of the burnt areas to regenerate naturally. Despite the substantial amount of published work regarding Thasos wildfires, there is no information related to post-wildfire effects on factors such as soil erosion. More research related to post-fire effects should help to an overall assessment of the negative impacts of wildfires on land degradation through processes such as soil erosion and flooding.Keywords: Erosion, land degradation, Mediterranean islands, regeneration, Thasos, wildfires.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 2262683 Data Embedding Based on Better Use of Bits in Image Pixels
Authors: Rehab H. Alwan, Fadhil J. Kadhim, Ahmad T. Al-Taani
Abstract:
In this study, a novel approach of image embedding is introduced. The proposed method consists of three main steps. First, the edge of the image is detected using Sobel mask filters. Second, the least significant bit LSB of each pixel is used. Finally, a gray level connectivity is applied using a fuzzy approach and the ASCII code is used for information hiding. The prior bit of the LSB represents the edged image after gray level connectivity, and the remaining six bits represent the original image with very little difference in contrast. The proposed method embeds three images in one image and includes, as a special case of data embedding, information hiding, identifying and authenticating text embedded within the digital images. Image embedding method is considered to be one of the good compression methods, in terms of reserving memory space. Moreover, information hiding within digital image can be used for security information transfer. The creation and extraction of three embedded images, and hiding text information is discussed and illustrated, in the following sections.
Keywords: Image embedding, Edge detection, gray level connectivity, information hiding, digital image compression.
Procedia APA BibTeX Chicago EndNote Harvard JSON MLA RIS XML ISO 690 PDF Downloads 2148